CEVO Client Information Disclosure
tl;dr
CEVO was a global eSports company built around North America’s largest competitive online PC gaming league. The CEVO client is software that is mandatory to be run during online play. The client was transmitting user authentication details (usernames and passwords) and private conversations in clear text which made them susceptible to eavesdropping attacks.
Good day CS:GO friends!
Reference: /r/globaloffensive post about ESEA’s password security from early spring 2015.
I had a couple of the guys over this weekend to play some video games and of course CS:GO was on our list. We decided to download the CEVO client because of the cost of ESEA and our skill differences in matchmaking. I recalled a Reddit post from this spring and decided to double check that CEVO would at least take the lessons learned from the attacks on ESEA and secure their users. I was wrong!
While the CEVO website has enabled HTTPS, [arguably] the most important part of their business, the client, is verifying login details and more in plain ol’ HTTP. How does that work?
Whenever a client authenticates with a website or web based application, typically, an HTTP POST request is generated. The HTTP POST request contains your account credentials (email address for CEVO, username for ESEA) and password. This is completely normal. The big difference here is that services like Google, Facebook, banks, .etc, use TLS (transport layer security) to encrypt the data between your computer and the server responsible for performing the authentication so no one else can see it; CEVO does not.
Not only does the client not encrypt login credentials, all communication over the client happens over HTTP which means your private messages are also disclosed to whoever is listening.
So what? Who cares?
With things like prize pools totaling over USD$150,000 and the CS:GO skins gambling economy, it would be trivial for a malicious person to harvest professional players’ information from large CEVO events and use that information to DoS an entire event for fun and profit!
How can I check?
If you’re not that savvy with Linux you could always use something like Fiddler or Wireshark to do the heavy lifting for you if. Here’s what fiddler looks like:
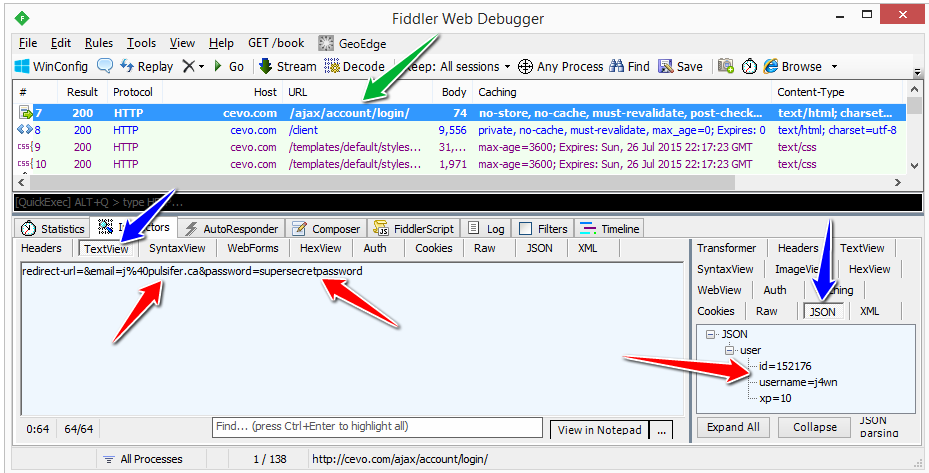
Fiddler showing HTTP results
If you prefer the command line, use something like tcpdump and string search your way to freedom.
| |

tcpdump showing usernames and passwords
So, until this gets fixed, I would exercise extreme caution when logging in via the CEVO client to play some games, especially on a network that you do not trust. It’s fixed 😄